What is DDoS?
You often hear the word DDoS, but before you understand DDoS, you must first know what a DoS attack is.DoS is a denial-of-service attack. It is a kind of network attack, the main purpose of which is to exhaust the network or system resources of the other party's computer, resulting in interruption and stop of services, making other users unable to access, and causing huge losses to enterprises.
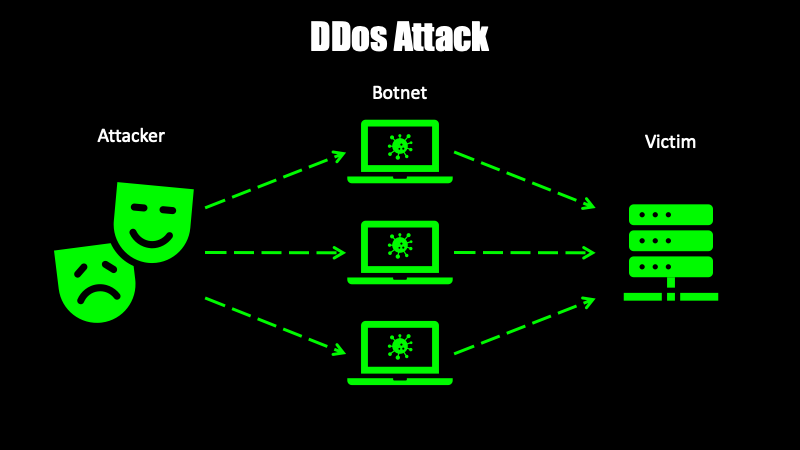
The full name of DDoS attack is distributed denial-of-service attack (distributed denial-of-service attack), by which hackers treat two or more compromised computers as zombies and launch specific targeted attacks. Usually DDoS attackers mostly target important services and well-known websites, such as banks and credit card payment gateways.
How can I tell if I have been DDoSed?
- Unusually slow internet (opening files or accessing websites)
- A specific website cannot be accessed
- Unable to access any website
- Rapid increase in spam
- The wireless or wired network connection is abnormally disconnected
- Denied when trying to access the website or any internet service for a long time
- The server is easy to disconnect, get stuck, and the access speed is delayed
There are three types of DDoS attacks
The three attack methods are bandwidth consumption type, resource consumption type, and vulnerability trigger type.
| bandwidth consumption | resource consuming | Vulnerability-triggered |
|---|---|---|
| This attack can be subdivided into a flood attack or an amplification attack. The former uses bots to send large amounts of traffic to compromised victim systems in order to block their broadband. The latter restricts the bandwidth of the victim's system by maliciously amplifying traffic. | This attack causes the victim's server to repeatedly and ineffectively operate. As a result, the web resources are exhausted, and the requests and needs of other normal users can no longer be responded to. | This attack is a denial-of-service attack by attempting to trigger vulnerabilities such as buffer overflows, causing core errors or blue-white crashes of the operating system. |
Qirui Technology | Your Internet Security Goalkeeper

Qirui Technology has a professional IT team with more than 20 years, providing a full range of solutions. The application fields include government, education, finance, medical care, e-commerce, games, and technology. And imported internationally renowned public cloud services and computer room hosting, connecting private clouds and hybrid clouds, in response to the ever-changing information security problems, there are also CDN, DDoS and vulnerability scanning, dedicated to bringing you the best solution!
Qirui Technology has a variety of CDN technologies and can provide multiCDN advice and services for enterprises. Over the years, it has assisted many projects such as cross-border e-commerce, service websites, and Chinese network optimization. It has a strong background and experience. Please click the button below to learn more Lots of content!
- Taiwan/China/Hong Kong/Singapore/Japan/Korea high-speed nodes
- Accelerate online games and e-commerce transactions
- Improve website protection power
- Avoid malicious traffic attacks
- 7×24 customer service online anytime




