APIs are targeted
API (Application Programming Interface), also known as "Application Programming Interface", is an indispensable element in current software applications and web applications. You can find it in the weather forecast on the website, or on the delivery platform. It, API has been unknowingly flooded with applications in all corners of life. According to statistics, in 2021, 41% of enterprises in the world will have API security incidents. Enterprises face risks such as leakage of sensitive customer information, data exposure Theft, data tampering, etc.
With the increasing use of APIs, more and more attackers will target the company's API vulnerabilities. The following are the top ten information security vulnerabilities of API Security announced by OWASP in 2019, hoping to help enterprises, development teams and information security teams Better understand the weaknesses that attackers often attack and take precautions against them!
OWASP API SECURITY TOP 10
| 2019 ranking | API Security Vulnerability |
|---|---|
| 1 | Broken object level authorization |
| 2 | Broken user authentication |
| 3 | Excessive data exposure |
| 4 | Lack of resources & rate limiting |
| 5 | Broken function level authorization |
| 6 | Mass assignment |
| 7 | Security misconfiguration |
| 8 | Injection |
| 9 | Improper assets |
| 10 | Insufficient logging & monitoring |
1st place Broken object level authorization
To crack the authorization of insecure objects, too loose Object ID will allow attackers to control the client to send Object ID request to access the information that should not be accessed, and then steal the data.
Second place Broken user authentication
For identity authentication cracking, API identity authentication needs to be different from the original endpoint identity authentication. Otherwise, it is very easy for an attacker to obtain access to the API by performing password permutation and combination cracking because of obtaining the user account and password.
3rd Excessive data exposure
Excessive data exposure is affected by the security design of the API. Whether other data beyond the client's authority is given due to the client's access, attackers can monitor the traffic through the network and analyze this to obtain these data.
Fourth place Lack of resources & rate limiting
Due to lack of resources and speed limitations, APIs are often used to query database data and return it. If the amount of data requested is too large, the operation speed will decrease in the case of lack of resources, causing other users to slow down or terminate services. An attacker could then exploit this vulnerability to disable services.
Fifth place Broken function level authorization
The authorization loopholes of different management levels, the complex hierarchical system and role management authority, and the ambiguous authority zone between managers and ordinary employees are easy for attackers to crack the rights of ordinary employees and obtain content that should not be obtained.
6th Mass assignment
Improper batch configuration. The API framework allows users to edit their own data, but does not lock the editing rights of other fields. Attackers can attack this vulnerability and edit account balances.
Seventh place Security misconfiguration
Security misconfigurations, common insecure defaults, allow unauthorized access to data and directories, exposing sensitive user information.
Eighth Injection
Injection attack, the attacker finds that the API can be attacked by injecting code, and can write some data-stealing code to make the API perform inappropriate actions.
9th place for Improper assets
Improper version control, the old version of the API has not been updated and has loopholes, attackers can obtain the method to enter the old version by means to avoid the new version to obtain data.
10th Insufficient logging & monitoring
Insufficient monitoring of logins, there is no immediate and effective detection and response to suspicious logins in the API, so attackers have enough time to damage the system.
How to protect against API security attacks?
At present, it is difficult to effectively defend against attacks by relying only on general API gateways, load balancing devices and WAFs. In addition to monitoring traffic in real time, it is also important to discover API vulnerabilities in advance. Currently, the world's largest API Security brand Noname provides a very complete service.

The Noname API Platform is an out of band solution that proactively protects your environment from hacker attacks due to API security vulnerabilities, misconfigurations, and design flaws, and provides API security through automated detection scans and quick responses Protect. Noname Security instantly protects APIs and detects vulnerabilities and misconfigurations before they can be maliciously exploited, integrating with your API gateways, load balancers and WAFs to provide deeper visibility and security.
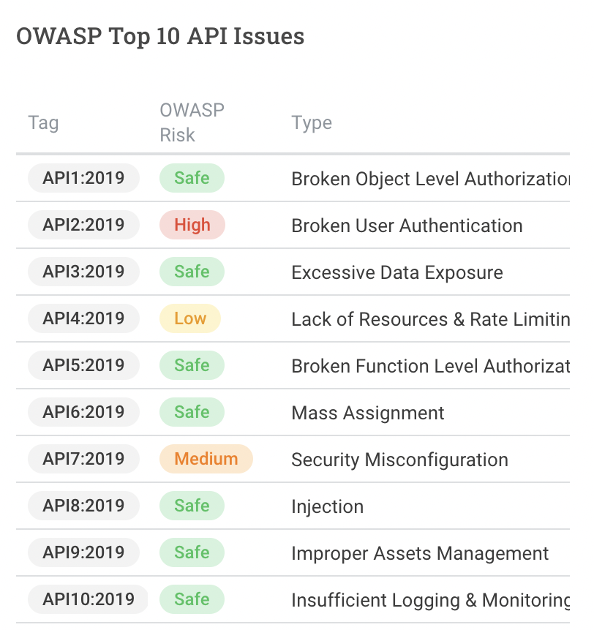
▲ Noname can analyze the number of all APIs and classify them, and also present the OWASP TOP 10 API security assessment on the report, to understand which aspects of the website are facing the most vulnerabilities.
Qirui Technology | Your Internet Security Goalkeeper

Qirui Technology has a professional IT team with more than 20 years, providing a full range of solutions. The application fields include government, education, finance, medical care, e-commerce, games, and technology. And imported internationally renowned public cloud services and computer room hosting, connecting private clouds and hybrid clouds, in response to the ever-changing information security problems, there are also CDN, DDoS and vulnerability scanning, dedicated to bringing you the best solution!




